What's a Load Balancer and why might it be useful for me?
A Load Balancer is usually put in front of your application servers and acts as the first point of contact for incoming requests. Depending on which algorithm it uses, it is then able to distribute traffic across your infrastructure. This results in increased availability, scalability and performance of your application.
Each Load Balancer has:
- Public IPv4
- Public IPv6
- Private IPv4 (if added to a private Network)
Which server IPs can be added as Load Balancer targets?
You can add the public or private IPv4 of a cloud server and the public or private IPv4 of a dedicated root server (Robot account) as a Load Balancer target.
Dedicated root servers always have to belong to the owner of the project the Load Balancer is in, and they have to be managed by the same account on Hetzner Robot. On Hetzner Console, the IP address of a cloud server is automatically taken from the project and added as a target. But for dedicated root servers, the user must manually enter the IP address as the target.
The following rules apply to private IP targets:
Cloud Server
- The cloud server and Load Balancer have to be in the same private Cloud Network.
Dedicated root server
- The dedicated root server and Load Balancer have to be in the same private Cloud Network (vSwitch).
- The private IP has to be within the IP range of the dedicated server's vSwitch subnet.
How many Load Balancers can I create?
Each customer has a default limit for the number of Cloud resources that we simultaneously provide. If you would like to increase your limit, you can send a request to our support team by opening a support ticket via Hetzner Console. Our team will quickly review your request and, if everything is in order, they will increase your limit.
How do you bill for Load Balancers?
We bill Load Balancers the same way as servers. They have both a monthly price cap and a price per hour.
What performance can I expect from Load Balancers?
Performance depends on your Load Balancer's configuration and workload (e.g. if you require TLS termination). Our Load Balancer plans are designed to deliver efficient and reliable distribution of traffic for most use cases.
The key factor to consider is the number of concurrent open connections each plan supports:
- LB11 up to 10,000 connections
- LB21 up to 20,000 connections
- LB31 up to 40,000 connections
Larger plans are allocated more CPU and memory to handle higher demand.
We do not explicitly limit bandwidth. However, all Load Balancers scheduled on the same node share a 2x10Gbit interface, which represents a hardware-based limitation.
Similarly, we do not explicitly limit the number of new connections over time. The connection rate is limited only by the system's resource constraints.
Choose a plan that matches your application's scalability and performance needs.
Is my Load Balancer highly available?
We designed Load Balancers to be highly available. If there is a hardware failure, an automatic failover will occur, and only a short service interruption will be visible to the clients.
Which protocols do Load Balancers support?
Our Load Balancers are capable of handling any TCP based traffic as well as HTTP and HTTPS. They speak HTTP/2 by default, depending on the client's capabilities.
If you configure the service of your Load Balancer with HTTPS, the encrypted connection will terminate at the Load Balancer (TLS Termination) and not at the target. To communicate with their targets, our Load Balancers use HTTP. To use HTTPS, you will have to use a TCP service.
For health checks, on the other hand, Load Balancers can use HTTPS.
What are health checks?
Health checks protect your application against single server failures by ensuring that traffic is only routed to healthy targets. There are two types of health checks: active and passive. Our Load Balancers support both.
Active health checks are configurable and actively check in certain intervals if the Load Balancers targets are still alive and responding to requests.
Passive health checks are checks that happen passively with every request that is forwarded from the Load Balancer to a target.
Once a target is deemed unresponsive and thus "unhealthy", it is no longer used to forward requests to. The active health checks continue though, and the target will be revived when passing the configured amount of times.
What does proxy protocol mean and should I enable it?
!! Switching proxy protocol on for targets which do NOT support it will render the whole service inaccessible !!
ProxyProtocol is used to transfer the connection information across multiple layers of connections. It can be used to forward the original client's IP address to the target service. For this to work, your listening software on the target must support this feature and have it explicitly enabled.
Here is an example for how to enable it for nginx: https://docs.nginx.com/nginx/admin-guide/load-balancer/using-proxy-protocol/
Do Load Balancers forward special HTTP headers?
If you choose protocol http or https, the Load Balancer will add these headers to the forwarded request:
- X-Forwarded-For - contains the IP address of the original client making the request
- X-Forwarded-Port - contains the listen port of the Load Balancer service. So if your Load Balancer listens on port 80, it will contain 80.
- X-Forwarded-Proto - contains the protocol the client used to contact the Load Balancer. Can be http or https.
These HTTP headers are not added when the protocol TCP is used.
How do I determine which IP address a request originally came from?
For service protocols http and https, the “X-Forwarded-For” HTTP header contains the IP address of the requesting client.
If your target service supports it, you can look into using the ProxyProtocol feature to find the IP address. For the service protocol TCP, this is the only option.
Can you send me the request log for my Load Balancer?
Load Balancers do not log individual requests for privacy, performance and cost reasons. This means, we do not have any request logs that we could send you. If you need detailed request logs, you need to setup the target servers accordingly yourself.
Can I assign a Floating IP to my Load Balancer?
Floating IPs only support cloud Servers as targets. Load Balancers themselves are highly available, so using a Floating IP is not necessary to achieve the best uptime.
Because we receive this feature request quite often, we are thinking about extending Load Balancers to support this feature in the future.
Are Load Balancers location bound?
No, targets within a Load Balancer do not have to be from the same location. Please note, however, that the Load Balancer has to be from the same network zone as its targets. IP based targets are only possible for Load Balancers in the eu-central network zone.
| Network zone | Locations |
|---|---|
ap-southeast |
Singapore (sin) |
eu-central |
Falkenstein (fsn1), Helsinki (hel1), Nuremberg (nbg1) |
us-east |
Ashburn, VA (ash) |
us-west |
Hillsboro, OR (hil) |
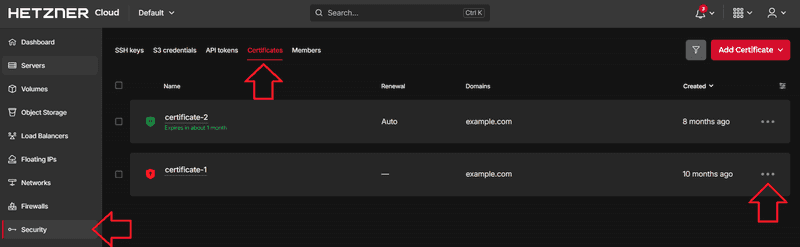
How can I manage my certificates?
You can manage your certificates in the Hetzner Console. Simply open your project and go to Security on the left menu bar. Then, go to Certificates on the upper menu bar and select Add Certificate.
You have two options:
-
Create certificate
This will create a managed Let's Encrypt certificate which will be automatically renewed by Hetzner. For this certificate, the domain name must be managed through Hetzner DNS. -
Upload certificate
You can also upload your existing certificate. You will have to monitor its expiration date and handle renewal yourself.
After a certificate has been added, you can use the options dropdown on the right to add labels and rename or delete the certificate.
Should there be an error, you can also use the options dropdown to retry.
What is a managed Let's Encrypt certificate?
For websites, a TLS/SSL certificate is used to prove the identity of the hosting server and verify that the communication between the client and the server is encrypted. This helps to protect sensitive information. Let's Encrypt is an organization that issues these TLS/SSL certificates for free. Once a certificate has been issued for a certain domain, the URL will begin with an https, with s being short for secure. Additionally, there will be a green lock right next to the URL.
On Hetzner Cloud you can add TLS/SSL certificates to your projects. You can either upload an existing certificate, or you can create a new one. If you choose to create a new certificate, a Let's Encrypt certificate will be created and managed for you by Hetzner. This is the managed Let's Encrypt certificate.
What do I need for a Let's Encrypt certificate?
To get a Let's Encrypt certificate, you need a domain (example.com), a Domain Name System (DNS) and access to the hosting server.
Our managed Let's Encrypt certificates can only be created with a Hetzner DNS zone. You can either use Hetzner DNS directly or you can use an external DNS and delegate ACME challenge to Hetzner DNS.
The Domain Name System (DNS) basically contains a list of domains and the corresponding IP addresses. This information is stored on name servers that are accessible via the internet.
Hetzner DNS
You can create your own Hetzner DNS zones at dns.hetzner.com. To create a new zone, you need to already own a domain. The name servers of Hetzner DNS are called:
- hydrogen.ns.hetzner.com
- oxygen.ns.hetzner.com
- helium.ns.hetzner.de
The actual information of the DNS is stored on the name servers (ns). To create a certificate, the DNS has to answer correctly, so the name of the name servers should not be changed.
In order to administer your DNS entries using the Hetzner DNS Console, you will need to point to the Hetzner name servers from your legacy DNS provider. For more information, take a look at our documentation on the DNS Console
External DNS
If you have an external DNS, you can delegate ACME challenge to Hetzner DNS and use your Hetzner DNS zone to create a managed Let's Encrypt certificate. This tutorial about setting up a Let's Encrypt certificate on cloud Load Balancers explains how to create a Hetzner DNS zone and how to redirect an external DNS zone to the Hetzner DNS zone.
How can I delete a certificate for my Load Balancer?
You will not find it directly at the Load Balancer but in your Projects Security settings.
So first of all click on Security in the left hand menu. After that, select Certificates on the Top. You will then see a full list of your SSL Certificates configured in Hetzner Console. On the right of a certificate, when clicking on the 3 horizontal dots, you can choose to delete a certificate in the upcoming pop-up.
How can I add a certificate including the intermediate certificates?
To add a server certificate with all necessary intermediate certificates, combine the certificates. Here is how it works:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate(s))
-----END CERTIFICATE-----You can then paste this combined certificate to the certificate form.