Introduction
Hetzner Online's stateless firewall is a free security solution for your dedicated root server. On the customer administration interface Robot, you can use the firewall feature to define your own filtering settings for incoming and outgoing traffic.
With our stateless firewall, or static firewall, data packets are not unpacked; rather, the head of each individual packet is inspected, and depending on the pre-defined settings, the firewall will decide whether to allow or reject these packets. In this way, the firewall prevents unpermitted access to your server.
However, with firewalls, it is important to remember that they do not actually recognize attempted attacks themselves. They only enforce a set of pre-defined rules for network communications. In addition to our stateless firewall feature, Hetzner Online offers DDoS protection; therefore, you have yet another security guard to protect your dedicated root servers from Internet dangers.
The firewall for Robot customers (who use dedicated root servers) is configured to the switch port. By default, the firewall filters only IPv4 traffic, an additional IPv6 filter can be enabled via the Filter IPv6 packets option.
How do I activate the firewall?
You can activate the firewall by going to Main functions -> Servers. Then choose the server you would like, go to Firewall, and activate it. If you activate the firewall before entering any firewall rules, you will block all incoming traffic.
The firewall will immediately become active and will be configured to the switch. The configuration takes approximately 20-30 seconds.
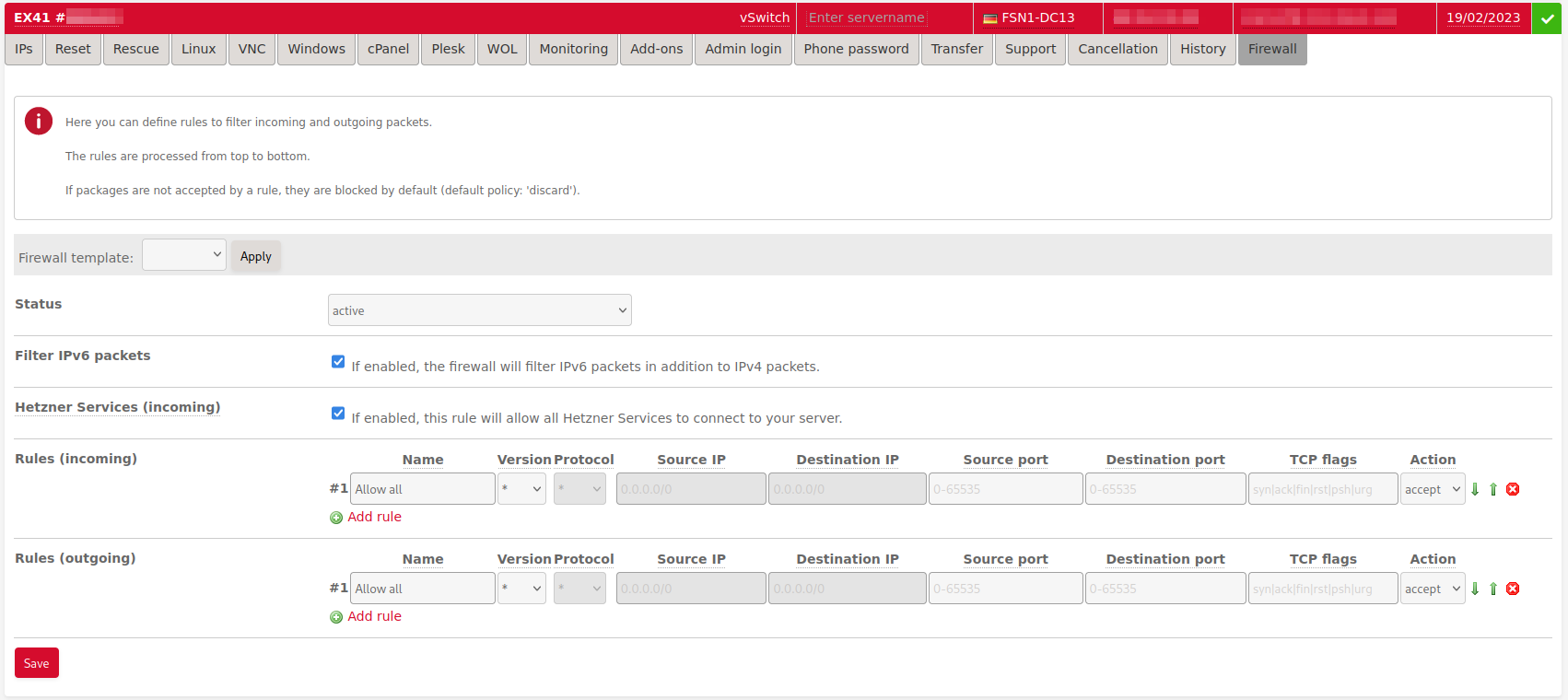
Firewall rules
You can use a maximum of 10 rules per direction.
Parameter
- Name: You can choose any name you like. Only special characters are not permitted.
- IP version: IPv4 or IPv6 or not specified (
*) - Protocol: Selection of protocol (for example, TCP or UDP).
- Destination IP and source IP: You can enter IP addresses either as single IPs or as a subnet in CIDR notation (for example,
<192.168.0.1>or<192.168.0.0/30>). Since the firewall is configured on the switch port, the rule without specified destination IP will apply to all IP addresses for the server. - Destination port and source port: You can enter ports as single ports or port ranges (for example, 80 or 32768-65535).
- TCP flags: You can enter TCP flags (syn, fin, rst, psh, urg) individually or as a logical combination (
|for logicalOR= At least one of the flags must be set;&for logicalAND= All flags must be set). - Action: The action defines what should happen with the packets when a rule applies, meaning it defines if the packets should be rejected (
discard) or if they should be forwarded (accept).
Prioritizing
Rules are applied in the same order as they are defined in Robot. They are executed from top to bottom. You can change the order of the rules after you enter them by using the green arrow icons at the end of each rule.
If rule #1 does not apply, then rule #2 will be checked. If rule #2 also does not apply, then rule #3 will be checked and so on until one rule applies and the packet is either discarded or accepted in accordance with the defined action. If the second rule applies, for example, then all rules after that will not be checked. If none of the rules apply, then the packet will be discarded.
Enabling Hetzner Services
By clicking on the checkbox Hetzner Services, you can activate all important infrastructural services from Hetzner Online without having to do any additional configuration. If you activate this option, services such as the Hetzner Rescue-System, DHCP, DNS, System Monitor (SysMon) will no longer be blocked, but will rather be enabled.
Please note that the infrastructure services can only be enabled for incoming packets. If you should also filter outgoing packets, additional rules are required to allow the response packets from your server to the Hetzner services. For more information, see Notes on stateless firewall.
IPv6 Filter
The IPv6 filter can be activated via the "IPv6 filter" checkbox.
Please note that when the IPv6 filter is activated, all IPv6 traffic is blocked if no rules for IPv6 packets have been created yet.
If you do not specify an IP version for a rule, then the rule applies to both IPv4 and IPv6.
Limitations IPv6
- It is not possible to filter the ICMPv6 protocol. ICMPv6 traffic to and from the server is always allowed. It is necessary to allow ICMPv6 by default because ICMPv6 is an important auxiliary protocol and is mandatory for the operation of IPv6.
- For rules with IP version IPv6 or no specification of IP version, it is not possible to filter on destination and source IP address.
- Without specifying the IP version, it is not possible to filter on a specific protocol.
Notes about stateless firewall configuration
A stateless firewall only makes decisions about packets by inspecting individual packets. Therefore, the firewall doesn't "keep track of" whether or not an incoming packet belongs to an established connection. For this reason, unless you enter an additional rule, all outgoing connections from the server, and if you filter outgoing pakets all incoming connections to the server, will not work, because the respective answer packets in the opposite direction can no longer pass the filter.
Incoming direction
Without an additional rule, all answer packets coming to the server cannot pass the firewall.
You can use the following rule to generally allow all responses to TCP connections:
Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination port: 32768-65535 (Ephemeral Port Range)
Protocol: tcp
TCP flags: ack
Action: acceptBy entering IP addresses and TCP ports, you can, of course, make this rule more restrictive.
Example
The following rules are defined in the firewall:
Incoming: Only HTTP pakets allowed
Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination port: 80
Protocol: tcp
TCP flags: No entry
Action: acceptOutgoing: No restrictions
Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination port: No entry
Protocol: *
TCP flags: No entry
Action: acceptThe server <1.2.3.4> establishes a connection to the external webserver and sends the following TCP packet:
Source IP: 1.2.3.4
Destination IP: 4.3.2.1
Source port: 44563 (random port from the ephemeral port range)
Destination port: 80
Protocol: tcp
TCP flags: synIn this example, the outgoing packet is not blocked by the firewall at all since only incoming connections are filtered.
The webserver <4.3.2.1> responds with the following packet:
Source IP: 4.3.2.1
Destination IP: 1.2.3.4
Source port: 80
Destination port: 44563
Protocol: tcp
TCP flags: syn & ackThis packet is blocked without the additional rule. So a connection cannot be established.
Outgoing direction
Similar to Incoming direction, answer packets are not automatically allowed for the opposite direction.
If only certain outgoing packets are allowed, then without further rules, answer packets from the server to connection requests to server services will also be unable to pass through the firewall.
You can add a general rule for the outgoing direction to allow all answer packets:
Source IP: No entry
Destination IP: No entry
Quell-Port: No entry
Ziel-Port: 32768-65535 (Ephemeral Port Range)
Protocol: tcp
TCP flags: ack
Action: acceptPlease note that the ephemeral port range of all clients must be respected here, this may differ from the port range of the server.
As a further essential rule, it is also recommended to allow packets to the DNS service. Since the Hetzner Services option is only available for incoming rules, this traffic must also be enabled for Hetzner DNS servers in the outgoing direction.
Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination Port: 53
Protocol: udp
TCP flags: No entry
Action: acceptExample
The following rules are defined in the firewall:
Incoming: No restrictions
Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination port: No entry
Protocol: *
TCP flags: No entry
Action: acceptOutgoing:
Only HTTP and DNS traffic allowed.
Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination port: 80
Protocol: tcp
TCP flags: No entry
Action: accept Source IP: No entry
Destination IP: No entry
Source port: No entry
Destination port: 53
Protocol: udp
TCP flags: No entry
Action: acceptThe client 4.3.2.1 establishes a connection to your HTTP server 1.2.3.4.
Source IP: 4.3.2.1
Destination IP: 1.2.3.4
Source port: 44563 (random port from the Ephemeral Port Range)
Destination port: 80
Protocol: tcp
TCP flags: synThis packet can pass through the firewall, since incoming all traffic is allowed.
The server wants to respond to the connection request with a SYN & ACK packet:
Source IP: 1.2.3.4
Destination IP: 4.3.2.1
Source port: 80
Destination port: 44563
Protocol: tcp
TCP flags: syn & ackThis packet cannot pass the firewall in outgoing direction, because outgoing TCP traffic is only allowed to port 80.
The remedy is either a general rule as described above, or a special rule to allow only responses from the web server:
Source IP: keine Angabe
Destination IP: keine Angabe
Source port: 80
Destination port: 32768-65535 (Ephemeral Port Range)
Protocol: tcp
TCP flags: ack
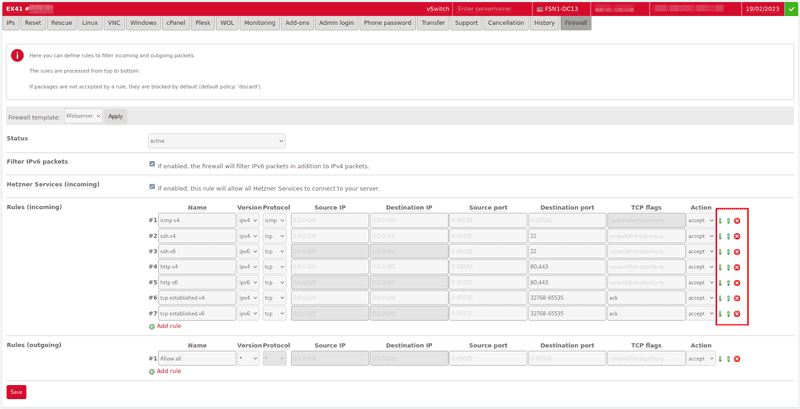
Action: acceptFirewall templates
If you click on the Firewall templates button in the server overview (Main functions -> Servers), you can create your own rulesets. Then you can paste these rules via the drop-down menu for the servers' firewall configuration and configure them.
In addition, there are several pre-defined example templates for common server services by default.
API
You can also configure your firewall via the Robot web service (API).